What Are Cookies

A cookie is a small file that a website places on your computer in order to store information. The entire process is harmless, and can also be helpful because cookies do useful things by saving you from the trouble of…
A cookie is a small file that a website places on your computer in order to store information. The entire process is harmless, and can also be helpful because cookies do useful things by saving you from the trouble of…
The list of apps to chose from for software developers seem to be increasing in number. Native apps, web apps and now it seems progressive web apps are the next in the list. In this blog, let’s take a brief look at…
Web Security also known as Cyber Security relates to the securing of websites and servers from online risks. It is aimed at safeguarding the sensitive data by restricting, discovering and responding to attacks. The website security check involves scanning for potential vulnerabilities…
Distributed denial-of-service (DDoS) attacks are malicious efforts to disrupt normal traffic of a specific server, network or service by overloading the target or its surrounding infrastructure with a flood of Internet traffic. The goal of any DDoS attack is to attain efficiency…
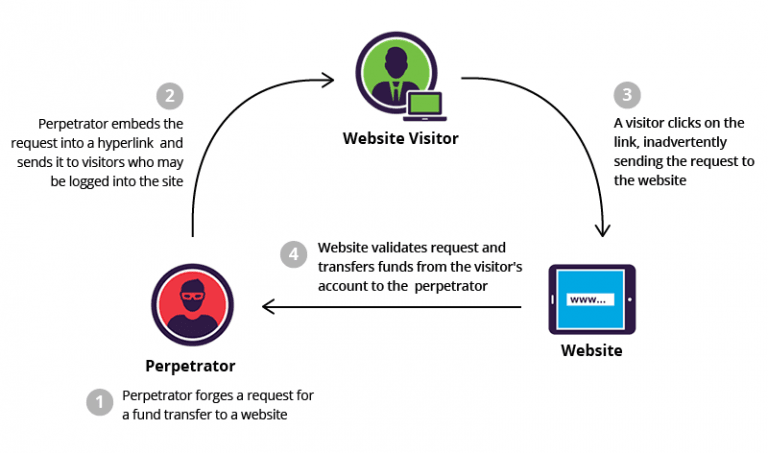
What is CSRF? Cross-site Request Forgery (CSRF), XSRF, or Sea surf is an attack on authenticated web applications using Cookies that tricks an end user to execute unwanted actions of the attacker’s choosing. The attack is especially aimed at state-changing…
Password Hacker refers to the individual who attempts to crack the secret word, phrase or string of characters used to gain access to secured data. Password hacking is often referred to as password cracking. In a genuine case, the password hackertries to…
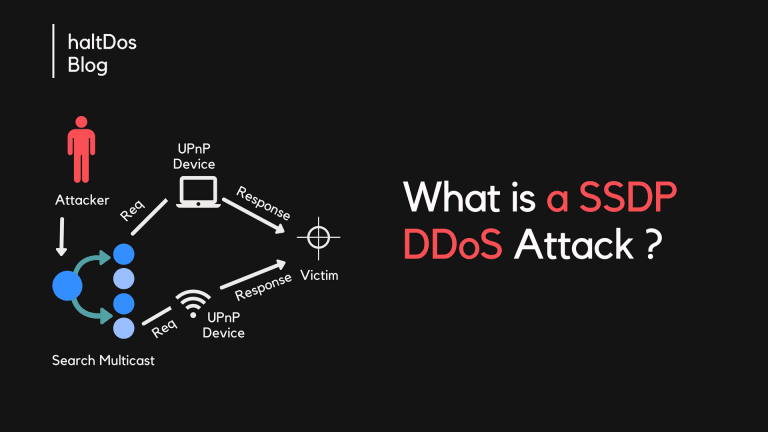
A Simple Service Discovery Protocol (SSDP) attack is a reflection-based distributed denial-of-service (DDoS) attack that can exploit Universal Plug and Play (UPnP) networking protocols to send a huge amount of traffic to a targeted victim, overpowering the target’s infrastructure and…
Spams and phishing emails are the most common method for the malware hackers to gain access to users’ credentials. its become so vicious and we have to be wary of clicking anything on the Internet. Malware authors create genuine looking…
In the computer world, a session refers to the temporary interaction between a user and the website. In other words, the in-between time of the log-in and log-off during the operation of an account is called a session. Session hijacking…
Distributed Denial of Service (DDoS) is a type of attack that involves using multiple compromised networks to target a single website. Hackers execute DDoS attacks by hijacking unprotected computers and installing malware. By using thousands of these “bots” or “zombie computers,”…